Which layer of the TCP/IP model is considered a segment?
Select Answer
Application Layer
Transport Layer
Network Layer
Data Link Layer
Which layer of the OSI Model uses Hubs to forward data to destination devices?
Select Answer
Data Link
Network
Transport
Physical
Imagine data is going up through the OSI model from layer 1 to layer 4. Choose the list that sequentially orders the PDU identifiers for each layer.
Select Answer
bits, frame, packet, segment
frame, packet, bits, segment
bits, packet, segment, frame
segment, bits, frame, packet
SMTP and POP3 use which protocol(s) to transfer information that guarantees delivery?
Select Answer
TCP
UDP
FTP
SNMP
Both TCP and UDP
A PDU represents the bits that include:
Select Answer
Only the encapsulated data for that layer.
Only the headers and trailers for that layer.
The headers and trailers for only the first layer, as well as the encapsulated data.
Only the headers for that layer.
The headers and trailers for that layer, as well as the encapsulated data.
The TCP/IP model's "Packet" would fall under what OSI layer?
Select Answer
L1PDU
L4PDU
L5PDU
L3PDU
Which layer of the OSI Reference Model defines end-to-end delivery of packets?
Select Answer
The Network layer
The Session layer
The Transport layer
The Link layer
The Ozone layer
The process of TCP on one computer marking a TCP segment as segment 1, and the receiving computer then acknowledging the receipt of TCP segment 1 is an example of what?
Select Answer
Data encapsulation
Same-layer interaction
Adjacent-layer interaction
OSI model
All of these answers are correct.
TCP, resides on what layer of the most current TCP/IP model?
Select Answer
Layer 3
Layer 2
Layer 4
Layer 5
IGMP, resides on what layer of the most current TCP/IP model?
Select Answer
Layer 3
Layer 2
Layer 4
Layer 5
What is the error-detecting code added to a frame in a data link communication protocol?
Select Answer
SMS
TCP
PPP
FCS
A _________ address is an address a single host listens to on a network.
Select Answer
Broadcast
Multicast
Unicast
Singlecast
What answer best describes Twisted Pair?
Select Answer
Twisting the cables together helps cancel out most of the EMI.
Not twisting the wire pairs together helps cancel out most of the EMI.
Twisting the wire pairs together helps cancel out most of the EMI.
Not twisting the cables together helps cancel out most of the EMI.
What are the types of IEEE standards for Ethernet that support Gigabit Ethernet?
Select Answer
802.3u & 802.3z
802.11b & 802.3u
802.3z & 802.3ab
802.3 & 802.11b
A commonly used header format for an Ethernet Frame consists of
Select Answer
Preamble FCS, Pad, SFD, Destination, Source, Type
FSP, Preamble, SFD, Destination, Source, Type
Preamble, SFD, Destination, Source, Type
Preamble, Destination, Source, Type
Fill in the blanks:
According to the IEEE 802.3 specification. The term ___ (MTU) defines the maximum Layer ___ packet that can get sent over a medium.
Select Answer
Maximum Transponder Unit | 4
Maximum Transfer Units | 3
Maximum Time Unit | 4
Maximum Transmission Unit | 3
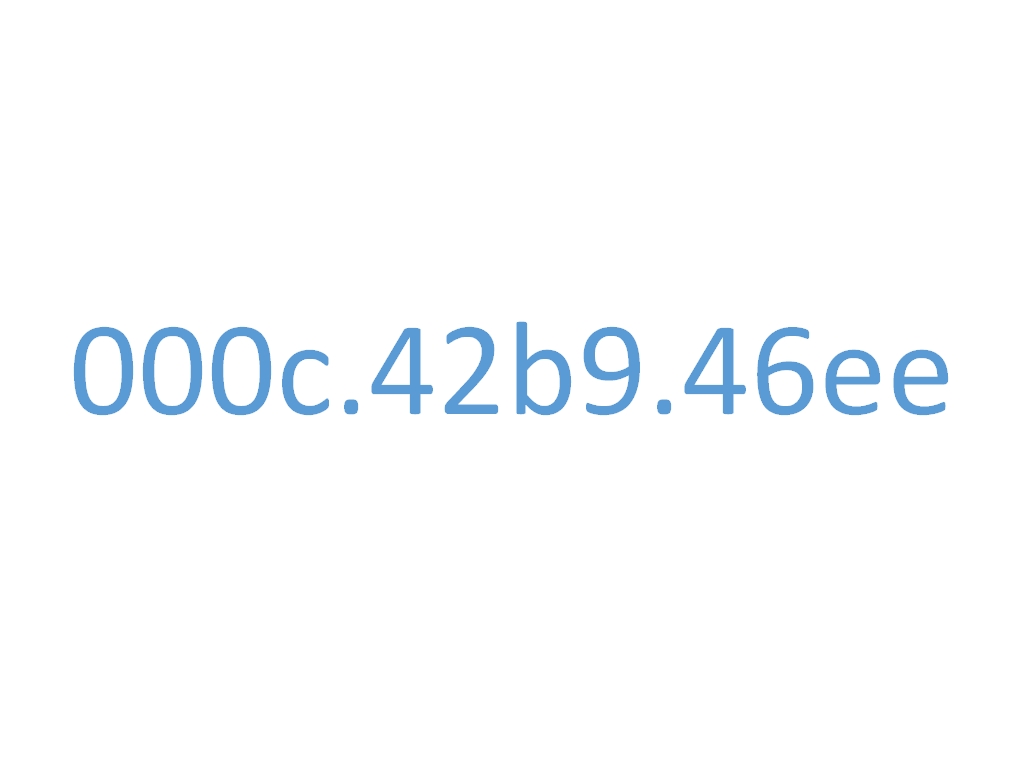
A device uses MAC address 000c.42b9.46ee. Which part of the MAC address indicates the originating networking equipment vendor?
Select Answer
42b9
b9.46ee
000c.42
000c
What type of cable is needed when connecting a Hub to a Router?
Select Answer
a straight-through cable
a crossover cable
a UTP cable
a fiber cable
What type of cable is needed when connecting a Switch to a Router?
Select Answer
a straight-through cable
a crossover cable
a UTP cable
a fiber cable
How many bytes are in the SFD field of an Ethernet frame?
Select Answer
7
1
6
2
Which protocol would typically be used for a client to find a server's IP address, based on the server's name?
Select Answer
DNS
DHCP
ARP
Ping
Why would a computer need to request information from a DNS server?
Select Answer
The computer requires an IP address to retrieve the information from the DNS.
It requires a name, to retrieve the information requested.
The computer needs to convert a name to an IP address.
The DNS acts as the middle man and converts the IP address to a name so a direct connection can occur.
Which of the following is the correct protocol for the ping command?
Select Answer
SNMP
ICMP
SMTP
RDP
When a host sends a packet to a host on a different subnet the host sends the packet to which of the following?
Select Answer
Sends the packet to DNS to determine how to forward the packet
Sends the packet to the DHCP to determine how to forward the packet
Sends the packet to the default gateway to determine how to forward the packet
Host will drop the packet as it cannot determine where to send the packet
Consider a host "PC1" is attempting to send a packet to another host "PC2". The two hosts are on the same subnet.
Which of the following is likely to occur?
Select Answer
The packet will get forwarded to the default gateway.
PC1 will use ARP to find information about the defualt gateway, then forward the packet directly to PC2.
PC1 will use ARP to find information about PC2, then forward the packet to PC2.
Consider PC1 is connected to VLAN 2 on switch SW1. Which of the following are in the same subnet typically?
Select Answer
The local router's WAN and all other PC's including PC1 attached to VLAN 2.
The local router's LAN and all other PC's including PC1 attached to VLAN 2.
Local router's LAN and all other PC's connected to SW1.
Local router's WAN, local router's LAN, and all PC's connected to SW1.
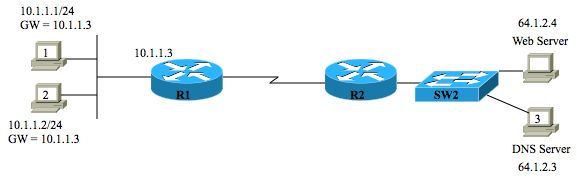
The exhibit shows the current contents of PC1's DNS cache and ARP cache. The user next opens a web browser to connect to URL www.ciscopress.com. Which of the following accurately describes the next packet sent by PC1?
|
DNS Cache: ARP cache: |
Select Answer
A DNS request sent to the DNS server's IP address
A DNS request sent to the 255.255.255.255 IP broadcast address
An ARP request looking for the DNS server's MAC address
An ARP request looking for the MAC address associated with 10.1.1.3 (R1)
How many Bytes are in the Flag of an HDLC frame?
Select Answer
1
2
4
8
How many Bytes are in the Type of an HDLC frame?
Select Answer
1
2
4
8
What is true about leased lines?
Select Answer
Provides permanent dedicated capacity
Offers high service quality
Costs more than newer WAN technologies
Removes latency and jitter
All of these are correct
Which of the following is the main difference between Telnet and SSH?
Select Answer
Telnet encrypts the password at login and SSH does not encrypt the password at login.
SSH encrypts the password at login and Telnet does not encrypt the password at login.
Telnet gets used when accessing a router or switch through a firewall and SSH is used within a LAN only.
SSH gets used when accessing routers and switches via a firewall or VPN, and telnet gets used within a LAN.
Which command is used to access context sensitive help in a Cisco switch or router?
Select Answer
help
/help
?
/?
After browsing to the end of the history buffer, you can use this option to display a more recently used command.
Select Answer
Down arrow
Ctrl-E
Ctrl-A
Up Arrow
Which type of memory used in Cisco switches?
Select Answer
RAM or DRAM
ROM
Flash memory
NVRAM
All of the above
All of the following commands will erase the contents of NVRAM, except?
Select Answer
write erase
erase startup-config
erase nvram
erase flash
When the Cisco IOS CLI is initially accessed via console, Telnet, or SSH, which mode is the user placed into?
Select Answer
User mode
Enable mode
Configuration mode
Boot mode
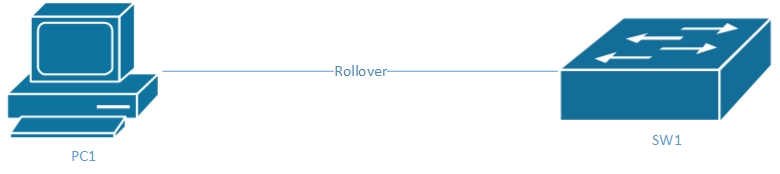
Refer to the diagram; which of the following connection parameters are used when connecting to the console of a Cisco switch?
Select Answer
9600, None, 8, 1
19200, None, 7, 1
9600, Even, 7, 2
19200, Even, 8, 2
Which Cisco command enables you to archive the local IOS on flash to an external file storage system?
Select Answer
archive
backup
ha-external
copy
failover
What comes before the value of the duplex and speed if they are determined by autonegotiation?
Select Answer
auto-
an-
a-
Fa-
Ga-
Refer to the exhibit. Based on the information shown in the exhibit, what can be said of the configuration of the Gi0/6 interface?
| Switch# show interfaces status Port Name Status Vlan Duplex Speed Type Gi0/1 notconnect 1 auto auto 10/100/1000BaseTX Gi0/2 connect 1 a-half a-100 10/100/1000BaseTX Gi0/3 notconnect 1 auto auto 10/100/1000BaseTX Gi0/4 connect 1 half 100 10/100/1000BaseTX Gi0/5 notconnect 1 auto auto 10/100/1000BaseTX Gi0/6 connect 1 a-full 1000 10/100/1000BaseTX |
Select Answer
The interface speed has been autonegotiated.
The duplex full command has been configured.
The speed 100 command has been configured.
The interface duplex has been autonegotiated.
What will a switch compare in its MAC table to be able to forward a frame?
Select Answer
Source IP address
Destination MAC address
Source MAC address
Destination IP address
You are working on interface VLAN 1 and want to enable it, which command works best to do so?
Select Answer
No shutdown
Enable interface vlan 1
Enable interface
Power on
No shutdown interface vlan 1
The password required to login to user mode through a console is called what?
Select Answer
vty password
user password.
user-mode password
default password.
console password.
Which answers encrypt the password that will be required of a user after they type the enable EXEC command?
Select Answer
enable password-value
enable password password-value
enable secret password-value
password password-value
Which error codes is unexpected on LAN switch physical interface?
Select Answer
- Line status: up
- Protocol Status: down
- Interface Status: not connected
- Line status: administratively down
- Protocol Status: down
- Interface Status: disabled
- Line status: down
- Protocol Status: down
- Interface Status: not connected
- Line status: down
- Protocol Status: down (err-disabled)
- Interface Status: err-disabled
Which counter is responsible for frames with an illegal format? (e.g.,. a partial byte)
Select Answer
Frame
Runts
Input errors
Output errors
Collisions
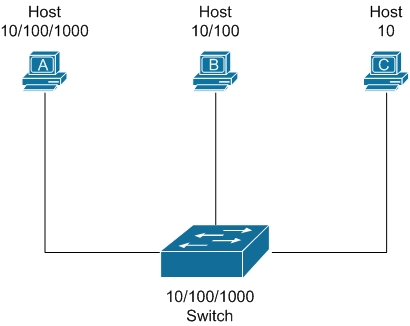
Refer to the diagram. Assuming autonegotiation is enabled, what would be the resulting speed and duplex of the link between the switch and Host A?
Select Answer
1000, Half
100, Half
1000, Full
100, Full
Refer to the exhibit. Which of the following commands has been configured on the displayed switchport?
|
Switch1#show interfaces Gi0/0 Switch1# |
Select Answer
disable
switchport shutdown
shutdown
port disable
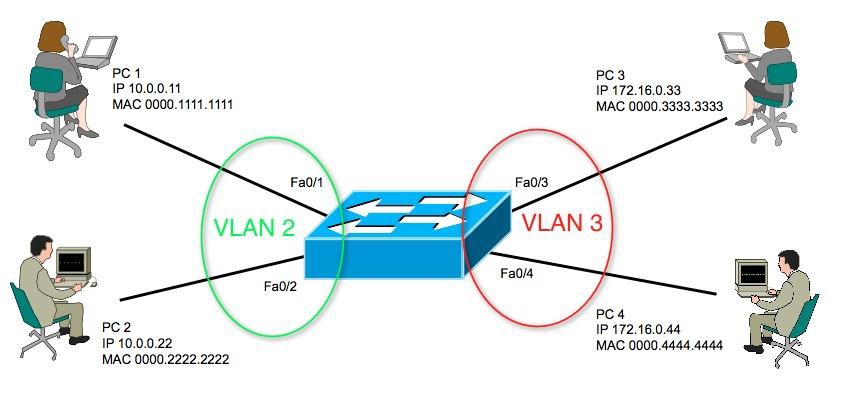
You want to stop PC 1 from being able to send and receive frames on the network. You issue the following commands:
SW1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# interface Fa0/11 SW1(config-if)# shutdown
PC 1 can still communicate on the network. Why?
Select Answer
The incorrect interface was configured.
The shutdown command does not make the switch stop sending frames to the PC, or stop processing frames received from the PC.
The command to disable a specific port is issued from global configuration mode.
It may take up to 30 seconds for the switch to stop traffic that has established sessions.
Which Cisco IOS command can be used to display which VLANs are supported over a specific configured switch trunk?
Select Answer
show switchport trunk
show interfaces switchport trunk
show trunk
show interfaces trunk
QUESTION 1 of 50
Introduction to TCP/IP Networking
Which layer of the TCP/IP model is considered a segment?
Select Answer
Application Layer
Transport Layer
Network Layer
Data Link Layer
Which layer of the OSI Model uses Hubs to forward data to destination devices?
Select Answer
Data Link
Network
Transport
Physical
Imagine data is going up through the OSI model from layer 1 to layer 4. Choose the list that sequentially orders the PDU identifiers for each layer.
Select Answer
bits, frame, packet, segment
frame, packet, bits, segment
bits, packet, segment, frame
segment, bits, frame, packet
SMTP and POP3 use which protocol(s) to transfer information that guarantees delivery?
Select Answer
TCP
UDP
FTP
SNMP
Both TCP and UDP
A PDU represents the bits that include:
Select Answer
Only the encapsulated data for that layer.
Only the headers and trailers for that layer.
The headers and trailers for only the first layer, as well as the encapsulated data.
Only the headers for that layer.
The headers and trailers for that layer, as well as the encapsulated data.
The TCP/IP model's "Packet" would fall under what OSI layer?
Select Answer
L1PDU
L4PDU
L5PDU
L3PDU
Which layer of the OSI Reference Model defines end-to-end delivery of packets?
Select Answer
The Network layer
The Session layer
The Transport layer
The Link layer
The Ozone layer
The process of TCP on one computer marking a TCP segment as segment 1, and the receiving computer then acknowledging the receipt of TCP segment 1 is an example of what?
Select Answer
Data encapsulation
Same-layer interaction
Adjacent-layer interaction
OSI model
All of these answers are correct.
TCP, resides on what layer of the most current TCP/IP model?
Select Answer
Layer 3
Layer 2
Layer 4
Layer 5
IGMP, resides on what layer of the most current TCP/IP model?
Select Answer
Layer 3
Layer 2
Layer 4
Layer 5
What is the error-detecting code added to a frame in a data link communication protocol?
Select Answer
SMS
TCP
PPP
FCS
A _________ address is an address a single host listens to on a network.
Select Answer
Broadcast
Multicast
Unicast
Singlecast
What answer best describes Twisted Pair?
Select Answer
Twisting the cables together helps cancel out most of the EMI.
Not twisting the wire pairs together helps cancel out most of the EMI.
Twisting the wire pairs together helps cancel out most of the EMI.
Not twisting the cables together helps cancel out most of the EMI.
What are the types of IEEE standards for Ethernet that support Gigabit Ethernet?
Select Answer
802.3u & 802.3z
802.11b & 802.3u
802.3z & 802.3ab
802.3 & 802.11b
A commonly used header format for an Ethernet Frame consists of
Select Answer
Preamble FCS, Pad, SFD, Destination, Source, Type
FSP, Preamble, SFD, Destination, Source, Type
Preamble, SFD, Destination, Source, Type
Preamble, Destination, Source, Type
Fill in the blanks:
According to the IEEE 802.3 specification. The term ___ (MTU) defines the maximum Layer ___ packet that can get sent over a medium.
Select Answer
Maximum Transponder Unit | 4
Maximum Transfer Units | 3
Maximum Time Unit | 4
Maximum Transmission Unit | 3

A device uses MAC address 000c.42b9.46ee. Which part of the MAC address indicates the originating networking equipment vendor?
Select Answer
42b9
b9.46ee
000c.42
000c
What type of cable is needed when connecting a Hub to a Router?
Select Answer
a straight-through cable
a crossover cable
a UTP cable
a fiber cable
What type of cable is needed when connecting a Switch to a Router?
Select Answer
a straight-through cable
a crossover cable
a UTP cable
a fiber cable
How many bytes are in the SFD field of an Ethernet frame?
Select Answer
7
1
6
2
Which protocol would typically be used for a client to find a server's IP address, based on the server's name?
Select Answer
DNS
DHCP
ARP
Ping
Why would a computer need to request information from a DNS server?
Select Answer
The computer requires an IP address to retrieve the information from the DNS.
It requires a name, to retrieve the information requested.
The computer needs to convert a name to an IP address.
The DNS acts as the middle man and converts the IP address to a name so a direct connection can occur.
Which of the following is the correct protocol for the ping command?
Select Answer
SNMP
ICMP
SMTP
RDP
When a host sends a packet to a host on a different subnet the host sends the packet to which of the following?
Select Answer
Sends the packet to DNS to determine how to forward the packet
Sends the packet to the DHCP to determine how to forward the packet
Sends the packet to the default gateway to determine how to forward the packet
Host will drop the packet as it cannot determine where to send the packet
Consider a host "PC1" is attempting to send a packet to another host "PC2". The two hosts are on the same subnet.
Which of the following is likely to occur?
Select Answer
The packet will get forwarded to the default gateway.
PC1 will use ARP to find information about the defualt gateway, then forward the packet directly to PC2.
PC1 will use ARP to find information about PC2, then forward the packet to PC2.
Consider PC1 is connected to VLAN 2 on switch SW1. Which of the following are in the same subnet typically?
Select Answer
The local router's WAN and all other PC's including PC1 attached to VLAN 2.
The local router's LAN and all other PC's including PC1 attached to VLAN 2.
Local router's LAN and all other PC's connected to SW1.
Local router's WAN, local router's LAN, and all PC's connected to SW1.

The exhibit shows the current contents of PC1's DNS cache and ARP cache. The user next opens a web browser to connect to URL www.ciscopress.com. Which of the following accurately describes the next packet sent by PC1?
|
DNS Cache: ARP cache: |
Select Answer
A DNS request sent to the DNS server's IP address
A DNS request sent to the 255.255.255.255 IP broadcast address
An ARP request looking for the DNS server's MAC address
An ARP request looking for the MAC address associated with 10.1.1.3 (R1)
How many Bytes are in the Flag of an HDLC frame?
Select Answer
1
2
4
8
How many Bytes are in the Type of an HDLC frame?
Select Answer
1
2
4
8
What is true about leased lines?
Select Answer
Provides permanent dedicated capacity
Offers high service quality
Costs more than newer WAN technologies
Removes latency and jitter
All of these are correct
Which of the following is the main difference between Telnet and SSH?
Select Answer
Telnet encrypts the password at login and SSH does not encrypt the password at login.
SSH encrypts the password at login and Telnet does not encrypt the password at login.
Telnet gets used when accessing a router or switch through a firewall and SSH is used within a LAN only.
SSH gets used when accessing routers and switches via a firewall or VPN, and telnet gets used within a LAN.
Which command is used to access context sensitive help in a Cisco switch or router?
Select Answer
help
/help
?
/?
After browsing to the end of the history buffer, you can use this option to display a more recently used command.
Select Answer
Down arrow
Ctrl-E
Ctrl-A
Up Arrow
Which type of memory used in Cisco switches?
Select Answer
RAM or DRAM
ROM
Flash memory
NVRAM
All of the above
All of the following commands will erase the contents of NVRAM, except?
Select Answer
write erase
erase startup-config
erase nvram
erase flash
When the Cisco IOS CLI is initially accessed via console, Telnet, or SSH, which mode is the user placed into?
Select Answer
User mode
Enable mode
Configuration mode
Boot mode

Refer to the diagram; which of the following connection parameters are used when connecting to the console of a Cisco switch?
Select Answer
9600, None, 8, 1
19200, None, 7, 1
9600, Even, 7, 2
19200, Even, 8, 2
Which Cisco command enables you to archive the local IOS on flash to an external file storage system?
Select Answer
archive
backup
ha-external
copy
failover
What comes before the value of the duplex and speed if they are determined by autonegotiation?
Select Answer
auto-
an-
a-
Fa-
Ga-
Refer to the exhibit. Based on the information shown in the exhibit, what can be said of the configuration of the Gi0/6 interface?
| Switch# show interfaces status Port Name Status Vlan Duplex Speed Type Gi0/1 notconnect 1 auto auto 10/100/1000BaseTX Gi0/2 connect 1 a-half a-100 10/100/1000BaseTX Gi0/3 notconnect 1 auto auto 10/100/1000BaseTX Gi0/4 connect 1 half 100 10/100/1000BaseTX Gi0/5 notconnect 1 auto auto 10/100/1000BaseTX Gi0/6 connect 1 a-full 1000 10/100/1000BaseTX |
Select Answer
The interface speed has been autonegotiated.
The duplex full command has been configured.
The speed 100 command has been configured.
The interface duplex has been autonegotiated.
What will a switch compare in its MAC table to be able to forward a frame?
Select Answer
Source IP address
Destination MAC address
Source MAC address
Destination IP address
You are working on interface VLAN 1 and want to enable it, which command works best to do so?
Select Answer
No shutdown
Enable interface vlan 1
Enable interface
Power on
No shutdown interface vlan 1
The password required to login to user mode through a console is called what?
Select Answer
vty password
user password.
user-mode password
default password.
console password.
Which answers encrypt the password that will be required of a user after they type the enable EXEC command?
Select Answer
enable password-value
enable password password-value
enable secret password-value
password password-value
Which error codes is unexpected on LAN switch physical interface?
Select Answer
- Line status: up
- Protocol Status: down
- Interface Status: not connected
- Line status: administratively down
- Protocol Status: down
- Interface Status: disabled
- Line status: down
- Protocol Status: down
- Interface Status: not connected
- Line status: down
- Protocol Status: down (err-disabled)
- Interface Status: err-disabled
Which counter is responsible for frames with an illegal format? (e.g.,. a partial byte)
Select Answer
Frame
Runts
Input errors
Output errors
Collisions

Refer to the diagram. Assuming autonegotiation is enabled, what would be the resulting speed and duplex of the link between the switch and Host A?
Select Answer
1000, Half
100, Half
1000, Full
100, Full
Refer to the exhibit. Which of the following commands has been configured on the displayed switchport?
|
Switch1#show interfaces Gi0/0 Switch1# |
Select Answer
disable
switchport shutdown
shutdown
port disable

You want to stop PC 1 from being able to send and receive frames on the network. You issue the following commands:
SW1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. SW1(config)# interface Fa0/11 SW1(config-if)# shutdown
PC 1 can still communicate on the network. Why?
Select Answer
The incorrect interface was configured.
The shutdown command does not make the switch stop sending frames to the PC, or stop processing frames received from the PC.
The command to disable a specific port is issued from global configuration mode.
It may take up to 30 seconds for the switch to stop traffic that has established sessions.
Which Cisco IOS command can be used to display which VLANs are supported over a specific configured switch trunk?
Select Answer
show switchport trunk
show interfaces switchport trunk
show trunk
show interfaces trunk
1:00:00
Your Exam is paused.
Please wait...
Since this is a preview of our actual test taking interface your progress cannot not be saved.